Artwork by Anonymous Media
Part 7: Abstract Ideas
By Josh Corman & Brian Martin
2012
If you are new to this series, please begin with Part 0 and the index.
NOTE: We will post each installment here for the security industry to garner feedback for about one week prior to posting to Forbes.com and a more mainstream and business readership. Please comment toward improving/clarifying the content.
In the first six articles, we have focused on objective observations and the concrete actions of Anonymous. In doing so, we hope to provide a better understanding of the group in order to help people make more rational decisions. However, the group’s more abstract ideas are important as well. Some of these considerations apply to Anonymous today, while some may apply to the Anonymous of tomorrow.
The authors of this article series have reached their opinions after lengthy discussion and debate. The thoughts presented in this article are our observations. We will be asking a lot of questions so that readers may reach their own conclusions.
How Will History Remember Anonymous?
They say “history is written by the victors” and “one man’s terrorist is another man’s freedom fighter”. So the big question is, how will Anonymous be remembered – and how will the story unfold?
In thousands of years, we as a society have not readily agreed on many aspects of history. When a decisive work is written, it is only a matter of time before new evidence or perspectives surfaces, challenging the history that we ‘knew’. History being written by the victors is a form of revisionist history that is often subtle, and sometimes nefarious. In some cases, the actual events are not really disputed, but their interpretation certainly is. For example, do we celebrate Anonymous’ questionable means like we do the Boston Tea Party? That night saw a mob of criminals trespass and destroy property to protest a wide variety of political issues. What if the group of men that boarded the ships in Griffin’s Wharf were wearing Guy Fawkes masks instead of Mohawk Indian disguises?
In contrast, will Anonymous be a present day Black Hand moment? While few people today remember why the Black Hand was formed, what we do know is that their assassination of Archduke Franz Ferdinand was the spark that lit the world on fire – beginning World War I. As one author’s High School Western Civilization teacher put it. “Any spark could have ignited this fire. All of the kindling and tension and instability and entanglement of alliances upon alliances… any spark would do.” And many feel such tension today; with such global economic instability, distrust in government, distrust in corporations, joblessness, disenfranchisement, and entanglement. Is the kindling and kerosene similarly primed for a spark to escalate in undesired ways? Are participants in Anonymous sure they will come out the revolutionaries versus the villains of history?

Emergent Property (Cause vs Effect)
When we set out to research this series, we knew that Anonymous was a phenomenon that commanded attention and required better analysis and consideration than we had seen. At the time, our focus was to understand what it was and wasn’t, and where it was going. Over time, it has become clearer, that something like Anonymous was inevitable. When asked to explain where Anonymous came from in a single sentence, one author replied:
Anonymous is an emergent property of, and a malformed response to, the current state of society and global hyper-connectivity.
Maybe not a “malformed response”, but an as-of-yet sub-optimal and forming response. As an aside, we’re curious what you would say as a one-liner (using the comments below).
While this series has focused on what has emerged, it is equally (if not more) important to understand the drivers that gave rise to this emergence. Those same drivers and forces will continue to fuel and shape the evolutions and permutations of Anonymous – and subsequent groups. This is perhaps why we see Anonymous less as the final product of technology and society, but rather as a canary in the coal mine – or as a harbinger of what is to come next. Either way, Anonymous is very likely the natural extension of evolution by the Internet and its denizens.
Despite having extensive experience with hacker culture and its history, neither of the authors have credentials in disciplines such as Psychology, Sociology, Anthropology, Behavioral Economics, Complex Systems Theory, or even Social Media (if it exists). We believe it would be very useful to assemble such a cross-disciplinary brain-trust to better understand these root causes and drivers – lest we wish to remain passive and reactive to them.
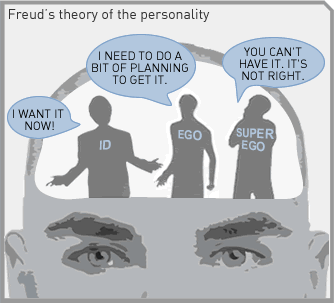
Paging Doctor Freud: The Id Unleashed
To date, pop-psychologist onlookers could characterize the bevy of Anonymous Operations as “the Id unleashed”. In the case of Anonymous, social media technology has been a force multiplier of their Id and angst. Individuals have been catalyzed to action, but without much of a common plan. In retrospect, this series was an attempt to highlight opportunities to progress Anonymous from Id to Ego to Super Ego more quickly – thus helping all affected parties.
Angst is Legion
To say many in Anonymous are stuck at the Id level presupposes one knows what they want, but that may not even be the case. Sure, there are pockets of themes, but very few are universally held within Anonymous. One of many intrinsic traits throughout Anonymous is angst.
Angst: a feeling of deep anxiety or dread, typically an unfocused one about the human condition or the state of the world in general — Oxford Dictionary
Note we did not assert that angst is unmerited. On the contrary, there are so many things that could cause angst that one cannot assume common root causes with their ad hoc peers – nor shared belief as to what to do about it. While cathartic, being angsty together doesn’t actually make it better – nor is it certain that you all share the same reasons for it. Stronger and more lasting bonds require greater cohesion than this superficial bond.
Groups require some basis of cohesion – some “glue” to bind them – some common ground. In lieu of a clear unifying objective, or explicit ideology, the clearest basis of common ground (aside from the obvious, ambiguous Rorschach-prone iconography) is that of shared, but unspecific anxiety and anger.
Valuable Ambiguity (Or is it?)
We’ve confronted this willful, prolonged ambiguity many times – in this series, at conferences, and in conversations with Anons. We were especially surprised to see some of Anonymous’ active resistance to define anything (as we suggest in Part 5) – even in the face of all the inherent limitations and challenges of keeping things ambiguous (as we outlined in Part 4). This willful ambiguity highlights that it is perceived to be valuable – perhaps even foundational. What is less clear is if the perceived benefits of ambiguity outweigh the actual costs or downsides of it.
Some have expressed that by keeping things undefined, they can attract greater numbers (Quantity vs Quality). Others want the freedom to keep it redefinable and malleable over time, for different groups to use the brand in the future. Some articulate good reasons for keeping it – others sound like they are making excuses. We’ve all worked with people who say “I’m flexible” when the realistic translation is “I have no plan and am too lazy / noncommittal to make one and I will probably end up messing up your plans later when I prove to be the opposite of flexible.” One of the most self-aware reasons we were given came from one of the more seasoned Anons: “We avoid stating our beliefs because we know we don’t agree – and it might cause us to ‘break up’.”
Irreconcilable Differences
Denial or avoidance of the ideological schisms within Anonymous does not make them go away. It may have once been tactically valuable to keep things undefined, but this does not hold long term. Some of the schisms are merely differences in style. Other schisms are substantive – even incompatible and irreconcilable. As we watched the pre-screening of We Are Legion, it was clear that some early rifts formed between those who wanted “lulz” and those who wanted a more moral calling. Later, several expressed their disdain for DDoS – believing that you can’t be anti-censorship and then censor others. In contrast, others in the film see DDoS as the foundation of internet-age free speech and protest.
This is one reason that the authors believe there will be several splinters that emerge out of the common pool – potentially defined by mission focus, but also by the revelations and recognitions of some of these incompatible differences. Substantive schisms are increasingly manifesting as participants begin to answer for themselves “What do I want?”
To Repair or to Destroy. (What Does Anonymous Want?)
It is unclear if Anonymous wants to destroy the system – or simply destroy the bad parts and fix them. The answer is probably “both”. We’ve even heard such from long standing members; “It depends on the day – and my mood”. While we can’t be certain, we suspect that post-arrest, Anons will hope to rely upon their innocence until proven guilty, a trial by their peers, their rights and due process. From feedback and interaction, we do know that some want to improve the corrupt parts and abuses of an otherwise useful system. We also know that some within are more aggressively nihilistic and/or anarchistic, and would like the entire system (good and bad) burned down.
In the near term, individual actions of the destroyer and the reformer may be compatible, but they are ultimately not aligned. A little bit of chaos can be a beautiful thing; a healthy thing. It can keep a system honest, living, and vibrant. Too much can destroy in moments what took centuries of blood and sacrifice to secure. With no easy way to ask the populous of Anonymous how they divide in objectives or ideology, how can those who want to improve the system know when they are assisting more destructive, undesirable, or nefarious elements? When would they know if they were truly serving someone else’s agenda?
Puppet-Masters and/or Old Power
At this point, many older, manipulative power brokers have recognized the opportunity that is represented by a nameless, faceless, asymmetric force such as Anonymous. This includes nation states, criminals and cartels, profiteers, intelligence groups, corporations, and longstanding political movements; many with deep pockets. This is not their first rodeo. They have hijacked (and will increasingly hijack) the brand and its participants. This is what they do. A few Anons have spotted this, and are overwhelmed and/or disheartened. Others may find themselves unwitting pawns of unnamed interests, many with very different ends in mind than their own.
Sound & Fury (and Fatigue)
Yesterday, June 25th, marked one year since the “retirement” of LulzSec and the end of the Summer of Lulz. Despite the sound and fury of countless attacks, many question the impact. Among those asking are strident and committed members of Anonymous who have grown frustrated and tired. Today one member volunteered this take on what others in the group are doing to undermine more measured efforts and time commitments:
“A bunch of fringe activists and nutters who rant about radical ideologies and conspiracies and do their best to create masses of fear instead of fostering unity and energy to cause movement.”
We’ve heard much of the same from others who have begun to focus on more specific and lasting change and impact.
Involvement
Traditionally, a group of people, be it activists or a knitting circle, has a clear line defining involvement. You are part of the group, or not, and there is no question about it. That simply doesn’t hold true with Anonymous. As we have discussed, there is no roster or membership guidelines. In addition, we have seen a wide variety of external influences on the group that forces us to reconsider what “involvement” means. This in turn leads us to consider a broad array of concepts about the group, the direction they are heading, and how they move forward.
Law enforcement (LE) is involved to varying degrees. As with any criminal group that comes under LE scrutiny, the investigation and pursuit influences the group. It causes them to change their tactics, take extra precautions, and may dictate what activities they carry out. If LE manages to turn a group member into a confidential informant, or places their own undercover agent in the group, LE has direct influence over how the group behaves, regardless of how passive they attempt to be. In the same vein, private intelligence firms that see opportunity in the actions of Anonymous (e.g., HBGary Federal) have a strong potential to influence the group in a variety of ways, both positive and negative. Even computer security firms that offer their opinions on Anonymous can influence the group.
The last element, and perhaps the most important in considering this idea, is the involvement of the average citizen. Increasingly, civilians are getting pulled into the group’s activities, like it or not. Operation BART, where Anonymous called for protests at BART train stations and ultimately leaked over 2,000 records of employees and customers, is one of many examples. In some cases, civilians were impacted trying to use the trains, while others had their private information posted to the Internet. Anonymous’ activity related to Occupy Wall Street, the war on Scientology, and dozens of other actions involve people from all walks of life (i.e. “collateral damage”). While civilians are not directly influencing Anonymous right now, we have previously argued that they should.
Everyone is involved, like it or not.
Influence
The idea of social manipulation is old. It is deeply ingrained in many cultures, in a wide variety of ways. For example, the last fifty years of American advertising have been dominated by psychology since John B. Watson joined J. Walter Thompson. Watson changed the field of advertising by making it more effective through appeal to three basic emotional response: love, fear, and rage. Jump to the last ten years; advertising and marketing is a science where unsuspecting consumers are psychologically manipulated through sound and images. We go through life seeing hundreds of advertisements a day, and we have absolutely no idea how we’re being influenced, directly or subliminally.
This leads us to the issue of influence and certainty in the context of a group like Anonymous. With everyone being involved in some form or another, each of us should question that involvement. Are we being manipulated? Are we being used? Do we really understand our own involvement in the saga of Anonymous? It is easy to dismiss these questions as absurd or far-reaching, but that dismissal is born out of a head-in-the-sand syndrome. Backing up a few steps to look at the bigger picture, can you even say with certainty who is really part of Anonymous, and who isn’t? The name has been co-opted by fringe elements, wannabes, computer criminals, law enforcement, and more. With such a nebulous metagroup to begin with, how are all of these other actors involved in the group make up?
If the group is truly made up of any person that has influence, or been influenced by, does it re-define the idea of the word “group” in this context? In Anonymous: Fact vs. Fiction, we previously mentioned the daunting threat of a modern day witch-hunt based on McCarthyism. If the definition of group is stretched to encompass anyone influencing it, how long before we hear suspected Anonymous members in court saying:
“I am not and have never been a member of Anonymous. I do not and have not adhered to the tenets of Anonymous. I have never followed the Anonymous party line.”?
Tyranny vs Chaos (Entanglement & Escalation)
Many (including Anonymous) have framed a conflict between the forces of Chaos and Order. What few realize is the entanglement and escalation between those extremes. Take for example, this quote from Commander X:
But I will choose chaos over tyranny any day.
However, chaos and tyranny can inspire each other. Anonymous is fueled (in part) by an allergy to a surveillance state and threats to a free and open internet. The actions and demonstration of will/might/aggression of chaotic actors, motivates and provides the justification for greater security and clamp down. These reactions, frequently poorly conceived, serve to incite more chaos – and the cycle continues. As such, turning up the volume can cause the very things individuals wish to avoid.
Like a Finger Trap, the harder each side pulls, the less likely we are to find a tenable balance of “organized chaos”. This is the basis of both the Vanity Fair Article by Michael Gross entitled “World War 3.0” and a DefCon 20 panel on the subject which aims to tackle how December’s ITU meeting in Dubai may threaten a internet freedom.

World War 3.0: Control vs Chaos (Source: Vanity Fair – May 2012 Issue)
Endgame Ethics vs Hypocrisy
In thousands of years, we as a society have not readily agreed on whether the ends justify the means. The questions become; will we ever? Does it matter? Or is this something we must resolve on a case by case basis, because the ends can justify the means? If the end is something we agree on, do we ignore the means and hope to enjoy the revisionist history?
This dilemma has been debated endlessly, and likely will outlast us all. Whether or not you agree with Anonymous’ perception of the ‘bad’ that they fight, one cannot really argue that every member believes in their individual cause and are fighting for it. On one hand, they attempt to do good by fighting perceived tyrants and injustice. On the other hand, they frequently break laws or harm innocents in the process. This juxtaposition is a central theme in most of the activity carried out by Anonymous. Remember, for many, the cause may be as simple as “for the lulz” or their right to troll. Meanwhile, it is often trivial to argue that their own actions in the fight are also ‘bad’. How do we resolve this?
Perhaps the notion of “an eye for an eye makes the world go blind” is better said as “an eye for an eye makes the world pay mind”. Do all Anons feel the same way?
Hymenoptera Christian Pirates (Why Analogies Fail)
A running theme in describing Anonymous is the caveats when using the word ‘group’. One of the better comparisons was made by Patrick Gray who said Anonymous was like 17th century piracy; “They sailed the high seas and pillaged. They had a common flag. But they WERE NOT A GROUP.” This analogy goes a long ways, but eventually doesn’t hold up. Earlier this year, we compared Anonymous to Christianity, citing there are the truly good and giving members of the religion, as well as the less than desirable Westboro Baptists, all of whom share the same basic beliefs. If we leave the analogy that simple, it works. While Anonymous may be completely different than any other concept or group, it helps society to relate to them if they can be put in a context that is already understood to some degree. We offer a new analogy, that may help understand how a ‘leaderless’ group can operate, and promptly show how it too doesn’t hold up.
Consider Anonymous more like the Hymenoptera order of insects, which encompasses bees and ants. Per Wikipedia, ant colonies are “sometimes described as superorganisms because the ants appear to operate as a unified entity, collectively working together to support the colony.” This is done without every ant receiving instructions from a central leader. Similarly, in a colony of bees, when a queen dies, she is replaced by a new queen. The new queen, one of many who could fill the role, steps in out of necessity rather than any desire. In theory, this is how Anonymous is “supposed” to work, according to some members. The real goal, hypothetically, is that while there is a leader, occasional leader, or group of leaders, they are simply no more relevant than any other member of the group. Their role can be filled by any member who wishes to step up. More importantly, the leader does not need to be distinct in name, and their identity is irrelevant. The Hymenoptera analogy sounds good on the surface, but gets shot down when you substitute Sabu, AnonyOps, or Topiary into the analogy. Polarizing and strong-willed leaders don’t just run the hive, they change the entire tone and behavior of the colony.
As a society, we must quickly move away from this old defective crutch, and stop using analogies that do not hold up to some level of scrutiny. While they may be convenient in a one minute conversation or a high-level news article intended to quickly describe a group to people unfamiliar with a topic, ultimately they cause problems and bias rather than help someone truly understand.
What If?
The core of this article series focuses on “Building a Better Anonymous”. Over the coming years, what if Anonymous adopted our ideas and worked to improve the group in the ways we outline? If Anonymous became an activist group that achieved all of their goals while staying within the established (and reasonable) laws, would we as a society embrace them? In the spirit of a “better” Anonymous, it is conceivable that in time the group could shed many of the negative emotions and actions associated with it. A more positive Anonymous that affects change primarily through legal means, and only turns to breaking the law as an absolute last resort, would be interesting. With positive change, while pushing for people to get involved in bettering aspects of corporate and government control, what is next?
Anonymous, the political party. You may quickly dismiss this as absurd, but it is no more unlikely than a group of people who pirate software, movies, and music becoming a legitimate political party. Consider the Pirate Party in Sweden. Members of Piratbyrån had previously founded the BitTorrent tracker, “The Pirate Bay”, arguably the longest running and most resilient file sharing site in 2003. In 2006, the Swedish Piratpartiet became the first legitimate pirate party. From “illegal” file sharing to political party in three short years. Now, the Pirate Party has moved to the U.S. in the form of JP Hollembaek, running for Massachusetts state representative slot. With that in mind, consider it again; Anonymous 2016.
Conclusion
It is our hope that this article demonstrates the wide range of issues that surround Anonymous; both as the group is today, and what they may become tomorrow. Entire books can be written on the subject of Anonymous, and some already have been (and debated). If Anonymous is the tip of the hacktivist group iceberg, then it is important that we begin to think about and prepare for what comes next.
Copyright 2012 by Josh Corman and Brian Martin. Permission is granted to quote, reprint or redistribute provided the text is not altered, appropriate credit is given and a link to the original copy is included. Custom graphic courtesy of Mar – sudux.com.
Should you feel generous, please donate a couple of bucks on our behalf to any 501(c)(3) non-profit that benefits animals or computer security.